On the 5th birthday of the Raspberry Pi last week, the foundation announced a new addition to the family — the Raspberry Pi Zero W. The W stands for Wireless.
I got my hands on one, from the fine folks at Pimoroni. (And no they didn’t pay me to say this.)
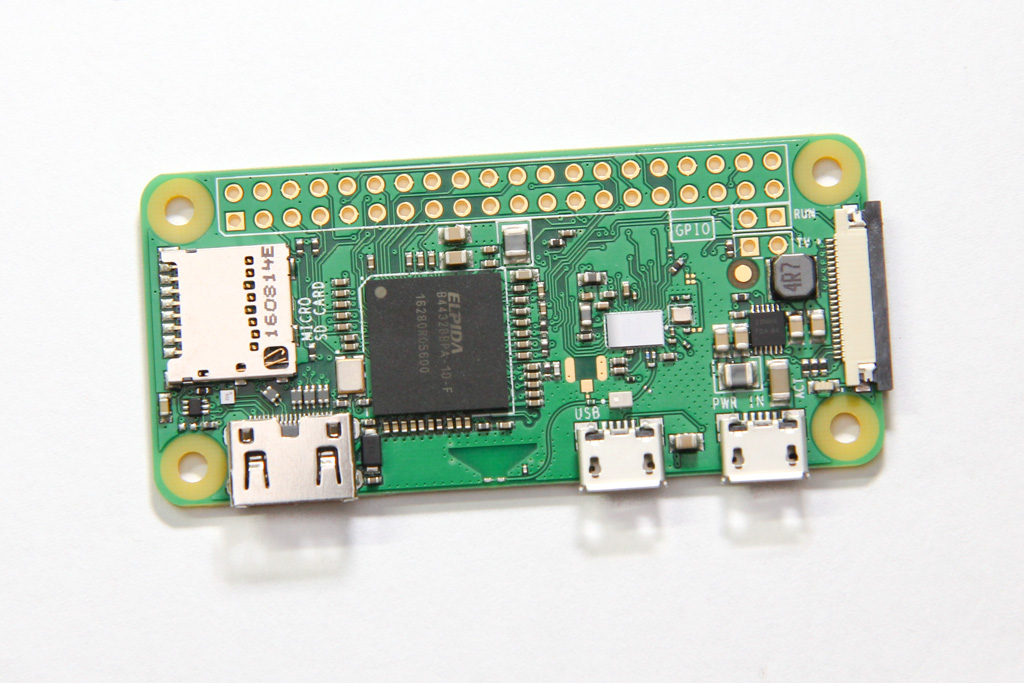
It has the same specs as the Raspberry Pi Zero, namely the 1GHz single-core CPU and 512 MB of RAM. It still has the two micro USB port — one for power and another for OTG, which means you can get it to behave like USB devices when plugged into a PC. The big difference is that they have added WiFi and Bluetooth capability to this small board by squeezing some space out from between the processor and the power circuitry. The size of the board and the placement of connectors remain the same, even the test points on the back.
I’m excited for anything that has processing power, HDMI connectivity and WiFi.
WiFi + Bluetooth
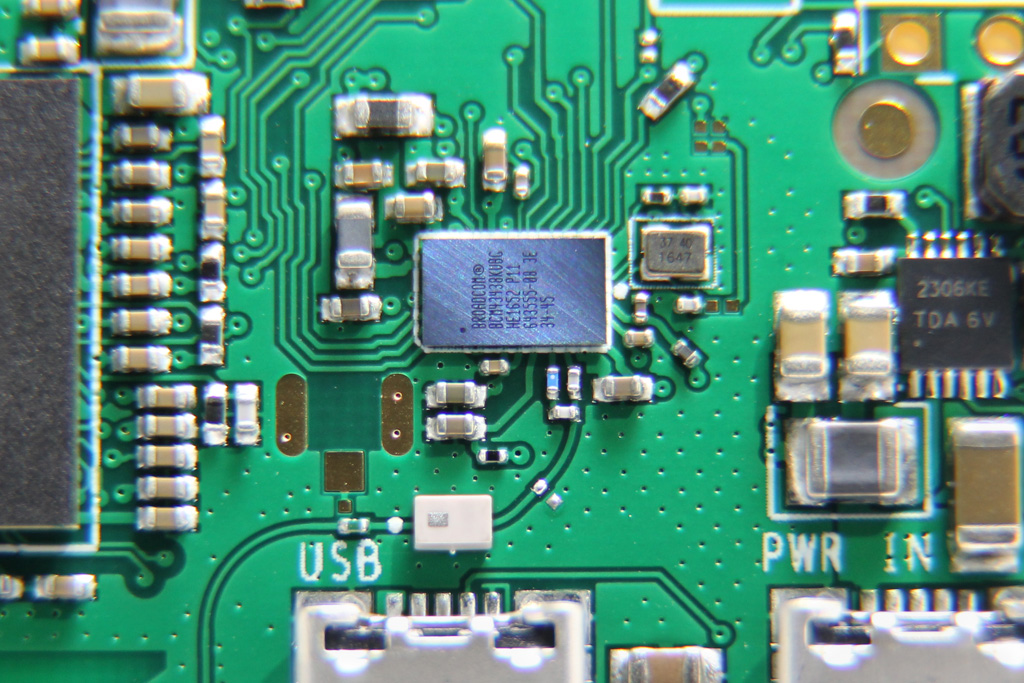
The 802.11n WiFi and Bluetooth 4.1 functionality comes from the Broadcom BCM43438 (now known as the Cypress CYW43438). This is the same chipset that was used in the Pi 3. The wireless chipset connects via SDIO, so your network traffic does not have to contend for the USB bus bandwidth.